Thursday, April 20, 2006
Alert! Spoofed Symantec Email Disables Anti-virus Updates
The email contained a "From" address that said it was from Symantec's Norton Anti-Virus division. The message said that the user's computer was infected with a virus called w32.aplore@mm. The user was then directed to a link that was supposed to dispose of the infection, but instead downloaded an executable file that disabled updates.
The malicious file was located on a free hosting service but the Web site mirrored a Symantec update site. The spoof was discovered by security company SurfControl.
Tuesday, April 18, 2006
Demand For Secure Web Environments For Kids Rises !!!
via Chris.
Wednesday, April 12, 2006
IE Cumulative Security Update Issued !
Microsoft issued a cumulative security update for Internet Explorer, replacing several earlier security updates. Rated: Critical
The update replaces a February 28th cumulative update affecting Windows XP Service Pack 2, Windows Server 2003 Service Pack 1, Windows XP Professional x64 Edition, Windows Server 2003 x64 Edition family, and Windows Server 2003 with Service Pack 1 for Itanium-based Systems.
Along with the update, Microsoft released a compatibility patch for Enterprise users who require more time to prepare for the Active X update. The compatibility patch will function until a subsequent Internet Explorer update is available in June. The changes made to Internet Explorer in relation to Active X will become permanent after the June update. A complete list of affected software and software components are available at the Microsoft bulletin page. Updates can be downloaded there as well.
Go directly to download page…
Tuesday, April 11, 2006
IE Address Bar Spoof Discovered!
An address bar spoof can be conducted by a malicious phisher taking advantage of a race condition in Internet Explorer.
The Secunia security advisory website advised IE users of a moderately critical vulnerability in the browser. Secunia created a test that can show if the user's browser is vulnerable.
IE 6 on fully patched Windows XP SP1/SP2 machines, and the IE 7 Beta 2 preview (March edition) demonstrate this vulnerability. In my testing, the vulnerability was present on IE 6, but not in Firefox 1.5 or Opera 9 TP2.
Like a previously reported critical issue about IE, Secunia noted that users can disable Active Scripting in the browser until Microsoft releases a patch. Secunia provided more details and a link to the test demonstrating the vulnerability:
The vulnerability is caused due to a race condition in the loading of web content and Macromedia Flash Format files (".swf") in browser windows. This can be exploited to spoof the address bar in a browser window showing web content from a malicious web site. 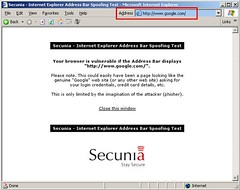
- Display of a spoof vulnerable IE -
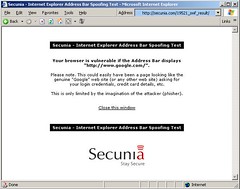
- Display of a spoof proof IE -
This is how your browser should look like! Check your browser!
Secunia has constructed a test, which can be used to check if your browser is affected by this issue: Click Here to Test your Browser!
Verify:
If u have doubts on a certain page u are browsing thru and wish to verify if its legitimate or not here’s somethin u can do ! just copy the code below and place it on the address bar u are viewing the page of doubt hit enter that will display the original page location!
<copy>
javascript:alert("The Real URL address: " + location.protocol + "//" + location.hostname + "/");
</copy>
Fix / Solution :
if u want a tool that can alert you wen there is a spoof like this then use the following toolbars they come in different flavors for different browsers :)
http://toolbar.netcraft.com/
http://toolbar.trustwatch.com/
http://www.corestreet.com/spoofstick/index.html
http://pages.ebay.com/toolbar/accountguard_1.html
http://addins.msn.com/addins_category_toolbar.aspx
Wednesday, April 05, 2006
Microsoft Says Recovery from Malware Becoming Impossible !
"When you are dealing with rootkits and some advanced spyware programs, the only solution is to rebuild from scratch. In some cases, there really is no way to recover without nuking the systems from orbit," Mike Danseglio, program manager in the Security Solutions group at Microsoft, said in a presentation at the InfoSec World conference. Offensive rootkits, which are used hide malware programs and maintain an undetectable presence on an infected machine, have become the weapon of choice for virus and spyware writers and, because they often use kernel hooks to avoid detection, Danseglio said IT administrators may never know if all traces of a rootkit have been successfully removed.
He cited a recent instance where an unnamed branch of the U.S. government struggled with malware infestations on more than 2,000 client machines. "In that case, it was so severe that trying to recover was meaningless. They did not have an automated process to wipe and rebuild the systems, so it became a burden. They had to design a process real fast," Danseglio added.
Danseglio, who delivered two separate presentations at the conference—one on threats and countermeasures to defend against malware infestations in Windows, and the other on the frightening world on Windows rootkits—said anti-virus software is getting better at detecting and removing the latest threats, but for some sophisticated forms of malware, he conceded that the cleanup process is "just way too hard."
![]() Microsoft says stealth rootkits are bombarding Windows XP SP2 machines. Click here to read more.
Microsoft says stealth rootkits are bombarding Windows XP SP2 machines. Click here to read more.
"We've seen the self-healing malware that actually detects that you're trying to get rid of it. You remove it, and the next time you look in that directory, it's sitting there. It can simply reinstall itself," he said.
"Detection is difficult, and remediation is often impossible," Danseglio declared. "If it doesn't crash your system or cause your system to freeze, how do you know it's there? The answer is you just don't know. Lots of times, you never see the infection occur in real time, and you don't see the malware lingering or running in the background."
He recommended using PepiMK Software's SpyBot Search & Destroy, Mark Russinovich's RootkitRevealer and Microsoft's own Windows Defender, all free utilities that help with malware detection and cleanup, and urged CIOs to take a defense-in-depth approach to preventing infestations.
![]() Are virtual machine rootkits the next big threat? Click here to read more.
Are virtual machine rootkits the next big threat? Click here to read more.
Danseglio said malicious hackers are conducting targeted attacks that are "stealthy and effective" and warned that the for-profit motive is much more serious than even the destructive network worms of the past. "In 2006, the attackers want to pay the rent. They don't want to write a worm that destroys your hardware. They want to assimilate your computers and use them to make money.
"At Microsoft, we are fielding 2,000 attacks per hour. We are a constant target, and you have to assume your Internet-facing service is also a big target," Danseglio said.